Aligning Risk Management and Threat-Informed Defense Practices (Part 1)
Cybersecurity is a complex field full of unique, specialized disciplines. There’s architecture and engineering, security operations, governance, risk management, and compliance (GRC), application security, offensive/red teams, and much more. Each discipline is laser focused on solving their portion of the puzzle. Along with the many disciplines that exist, come the multitude of ways organizations choose to approach the cybersecurity “problem”. The four most common team structures used to address cybersecurity are in-house, outsourced, “lone man”, and hybrid workforces. The in-house teams are a fully staffed cybersecurity department, with separate teams covering most of the disciplines mentioned above. Other companies choose to outsource their security functions to professional teams that have better talent, experience, resources, and knowledge available. Then there are the “lone man” teams, mostly small organizations that have just a few “do-it-all” cyber folks. And the final group of organizations will segment their internal team with outsourced or managed services, such as a SOC, MDR, or other _aaS (thing as a service).
No matter the approach taken, many teams struggle with cross-disciplinary communication and interactions. Truthfully, how often do our GRC teams and security operations teams interact? GRC might task SecOps to provide specific evidence or implementation details for a control, but that’s usually the extent of it. And it’s incredibly rare for SecOps to reach out to the GRC team for anything, “because compliance doesn’t equal security!” or so we’re all told.
In this blog series, I want to discuss the “what, why, when, how, and so what,” when it comes to aligning risk management practices with threat-informed defense principles and functions.
There are many reasons for the lack of collaboration between the security operations-focused teams and GRC. Some of the reasons I have come across include:
In larger or outsourced teams, it can often be implied “that’s not your job” so employees just don’t assist others or look to improve workflows that cross multiple teams
Environments can be so complicated that no one person really knows how everything should work together, and people assume others are responsible
Smaller teams are too busy to really dive deep into most tasks, having to work at “a mile wide and an inch deep” in knowledge and skillset
Management does not see the value in interacting across teams/units when those teams main functions differ
I believe that we’re missing a huge collaboration and partnership opportunity here. This alignment opportunity between GRC and SecOps is especially big for small businesses that have very limited resources for both compliance and security. In these cases it makes perfect sense for threat-informed defenses to be incorporated into compliance requirements. Any organization that knows its defenses and knows its adversaries is much more likely to defend effectively against attacks (or so our good friend Sun Tzu has told us).
Now you might wonder, “ok, but why should I listen to you?” And truthfully, I’m about as trustworthy as AI, but I have worked 15+ GRC-specific projects, spanning assessments, audits, and control implementation consulting. Those have covered multiple frameworks, including RMF (NIST 800-53), CMMC (NIST 800-171/172), FedRAMP, and ISO 27001. And for the past three years, I’ve been a security engineer focused on security data, think SIEM, detections, and CTI. So I have some experience in these seemingly contradictory domains of cybersecurity. Now I realize that this experience is probably not the “norm” when it comes to security professionals. So, as someone who has been on both sides of the cyber role spectrum, I wanted to discuss why and how companies can align their GRC efforts with threat-informed defense objectives (CTI, testing, and defensive measures).
However, before we can get into the real fun, we need to cover the “what?” In the following paragraphs we’ll go over a quick overview of GRC, threat-informed defense (TID), and MITRE ATT&CK. In future parts of this blog series we will take a look into why siloed teams are actually harmful to organizations, when it makes sense to align these functions, how to integrate a risk framework (in our case RMF) with MITRE ATT&CK, the expected benefits from this process, a few example workflows/use cases displaying how, some tools that are freely available to assist with these processes, and finally a few further recommended readings on this topic.
GRC Goals Overview
Governance, risk management, and compliance (GRC) teams work to assist organizations in staying secure, compliant, and strategically aligned. They work to manage risk by connecting business operations, cybersecurity, and regulatory requirements. GRC is often mandatory in organizations where regulatory pressure is high and risk tolerance is low. Think of regulated industries such as healthcare, finance, and government. One big aspect of GRC roles is working with compliance frameworks. There are plenty out there, and they typically will apply based on the industry or sector your organization is in. Just to name a few, we have RMF, CMMC, FedRAMP, GLBA, ISO 27001, HIPPA, GDPR, and PCI-DSS. All of these contain varying levels of specifications and focus, but if you search deep enough, in each you’ll find a list of controls, or security requirements an organization must be doing to achieve and maintain a certified state. We’re going to focus on the Risk Management Framework (RMF) for our discussion here. It is important to note, the DoD (or maybe it’s DoW?) has recently announced a replacement framework for RMF, the Cybersecurity Risk Management Construct (CSRMC). It doesn’t really change a lot, but does attempt to modernize the infuriating slow and manual processes that exist in RMF. You can read that announcement here: https://www.war.gov/News/Releases/Release/Article/4314411/department-of-war-announces-new-cybersecurity-risk-management-construct/.
The Risk Management Framework is a six-step process used to secure information systems by reducing the risk involved with operating those systems. It transforms certification and accreditation programs into a procedural lifecycle. RMF “provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle.” This is a very brief summary of RMF, more information can be found on the NIST website here: https://csrc.nist.gov/projects/risk-management/about-rmf.
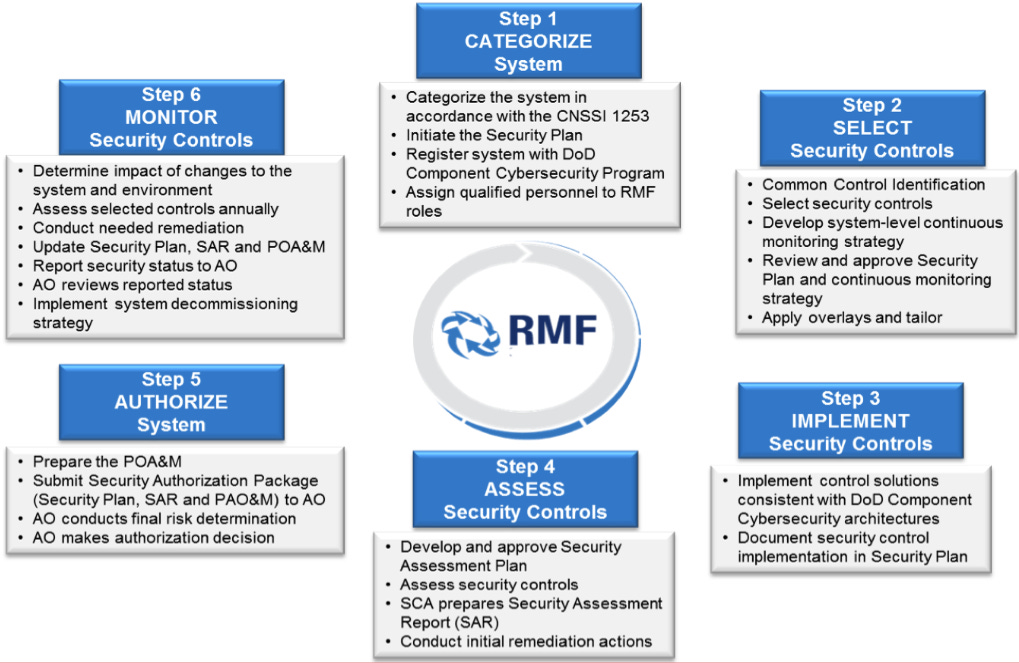
RMF was developed for the US government and is born out of NIST Special Publication 800-37 “Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy. RMF is the process used to assess, authorize, and maintain accreditation for all DoD systems, which includes IoT, OT/ICS, and other nonstandard systems. Everything has some level of risk involved with it, and it is impossible to completely remove all risks to an organization when operating a computer system. A system with no risk would be unusable. RMF seeks to assist in managing some of the risks associated with operating an information system. The six steps of RMF are Categorize, Select, Implement, Assess, Authorize, and Monitor. While used for all US federal systems, RMF has been adopted across multiple industries and countries as a standard for cyber defense. The framework involves the security controls that come from the NIST 800-53 Special Publication “Security and Privacy Controls for Information Systems and Organizations.” Even when an RMF accreditation is not required, it is very wise to use a framework of security controls, such as 800-53 or CIS, to implement defensive measures. The graphic below displays the six steps of RMF and what is performed in each step.
Like most risk frameworks and processes, the good intention is there. When analyzed, most of the RMF process makes sense. The real shortcomings are results of the 10-20 month processes that just will not work in cybersecurity. Things change too fast for “point in time” security to be an effective defense strategy.
TID Goals Overview
Now let’s cover the basics of threat-informed defense. I would happily describe it, but the following blog written by the Center for Threat Informed Defense (CTID) does this so well, that I’m just going to reference it below. You can read the full thing here: https://medium.com/mitre-engenuity/measure-maximize-mature-your-threat-informed-defense-64a51c2a869b
Here’s the cliff notes breakdown:
“Threat-informed defense is the systematic application of a deep understanding of adversary tradecraft and technology to improve defenses.
With MITRE ATT&CK® at its core, threat-informed defense encourages a focus on adversary behaviors, the specific actions that adversaries take to achieve their goals, recognizing that there are a limited number of behaviors and that these behaviors are common across adversaries and time. This behavioral focus allows defenders to make a critical shift towards an adversary perspective on their defenses and the tools and techniques that are available to achieve their goals. Defenders apply this knowledge to move beyond reactively chasing indicators of compromise and towards more effectively mitigating threats.
To implement an effective threat-informed defense, an organization must understand the threat and have an effective security plan in place. To understand the efficacy of existing or planned defenses and identify gaps, an organization must evaluate their current posture, as well as potential new measures, against the known threats. This process takes place in three main Dimensions:
1. Cyber Threat Intelligence (CTI) — understanding known behaviors of cyber adversaries; which specific adversaries are targeting its industry, technologies, or geography; and their motivations and typical objectives
2. Defensive (Counter) Measures (DM) — security actions put in place based on an understanding of the adversary; these could be technical (e.g. analytics, firewall rules, etc) or non-technical (e.g. policies, training, etc.)
3. Testing & Evaluation (T&E) — continuous assessments based on threat knowledge to validate defenses and illuminate gaps”
To best understand threat-informed defense, you need to understand the ATT&CK framework. For years, people used different terms to describe adversary tradecraft. To help solve this problem and allow for standardization within DFIR, MITRE created the ATT&CK framework. It is a collection of adversary tactics and techniques based on real-world observations. This globally accessible knowledge base has become the industry standard for identifying and labeling threat behaviors. MITRE ATT&CK allows organizations to identify the threats most applicable to them and how these threats operate, so that they may defend against them most effectively. ATT&CK has standardized threat behavior and offers information regarding specific APT groups, software/malware, cyber attack chains, and much more. With the ATT&CK matrix, organizations can plot each step of a cyber-attack.
The ATT&CK framework consists of Tactics, Techniques, and Sub-Techniques (or Procedures), which all sound very similar. To fully grasp the ATT&CK framework, knowing the distinction between these three terms is critical. It can get confusing, so let’s define TTPs:
Tactic – The technical goals of an adversary
Examples are: Reconnaissance, Initial Access, and Privilege Escalation
Technique – How those goals are achieved
Examples are: Phishing for Information (T1598), Scheduled Task/Job (T1053), and Data Encoding (T1132)
Sub Techniques (Procedures)- *Mostly* specific implementations of a technique
Examples are: Spear phishing link (T1598.003) and SSH (T1021.004)
ATT&CK may be used to map controls, identify defensive gaps, correlate CTI of adversary behaviors, and better understand/visualize attack chains and how adversaries move throughout an environment.
Why do I believe a threat-informed defense strategy is something organizations should pursue?
Threat-informed defense helps to match security goals and requirements with the top risks and threats facing an organization. Organizations may maintain an effective security approach that stays up-to-date and leads business and technology-related goals. Threat-informed defense also helps answer the questions:
What are adversaries doing?
How are they operating?
Can we detect them?
And can we stay one step ahead?
To properly answer those questions, an organization needs:
Clear visibility into the effectiveness of their security controls
Knowledge of adversaries and attack methods
The ability to test defenses and take proactive action on any identified weaknesses in processes and tools
A threat-informed approach to security allows an organization to measure the real capabilities of its security controls, and not just rely on a compliance score or vendor promises. They will have hard facts based on proof of tested controls against simulated adversary behaviors. Well, that’s all for now. In part 2 of this series, we’ll look at when and how to align GRC and TID functions.