Even if many plugins are fine, the bad ones are BAD
Sydney recently wrote a great piece about extensions and hunting for IDE plugins. I figured I could offer something similar for browser extensions… it's what I do every day now. She was absolutely correct that many extensions are generally harmless; however, I don't run into many organizations that don't have at least one extension doing something insidious. A browser extension can have even easier access to your most sensitive information like cookies and information on pages you visit (hey Salesforce!) than similar drive-by exploits.
Where do browser extensions come from?
Through the web store or add-on marketplaces, duh! What a dumb question! But wait… there’s more ways!
Extensions can also be sideloaded by enabling developer mode in a browser and importing a folder containing the extension. This is used by publishers when testing an extension before publishing.
As with all good things, this has been exploited by post exploitation tools to load in their own extensions. Luckily, as of Chrome version 137, all browsers have disabled the --load-extension launch flag commonly used by malware side load extensions. Check if you have any Chrome process executions with command line options containing this flag in the past! It will either be a developer, malware, or someone woefully obsessed with extensions.
Unfortunately, that is not the only method. Projects like ChromeAlone have methods of loading extensions by editing Chrome preferences files. This is quite sophisticated, but as a publicly available piece of software, it's bound to be used more often until that hole is plugged.
Sysmon 11 (File Create/Modify)
TargetFilename: C:\Users\[username]\AppData\Local\Google\Chrome\User Da ta\Default\Secure Preferences
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
If you use a management tool like Chrome Enterprise Core, it will tell you the means by which an extension was installed.
Exploring the open market
Let’s assume you’ve just started investigating an extension installed from a marketplace. You’re probably going to look at its listing first. What should you be looking for on those pages?
I’ll skip over some of the more obvious points like name squatting, type of
extension (please don’t install free VPNs), user counts, and reviews/ratings. While these are very relevant and helpful, know that they can also be deceiving, as attributes like user counts can be inflated and reviews can be faked.
Three things I would recommend not overlooking:
1. Know the publisher as well as you can: check if a domain is verified and whether the owner's email is from that domain.
2. Read the privacy policy: each extension is required to have one and many do state if your data is being captured or sold.
3. Identify whether an extension is private or unlisted: in the Chrome Web Store, extensions can be removed from indexing or shared with individuals by email address for 'testing'.
The blueprint for detection
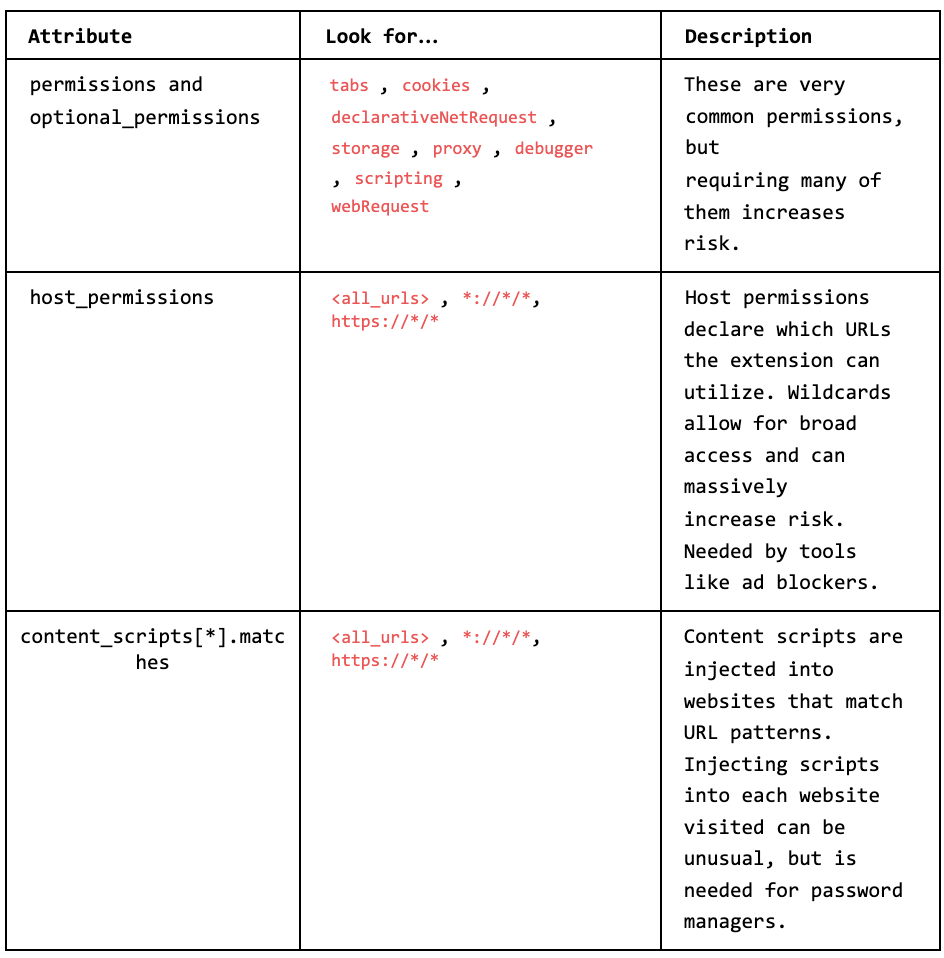
Browser extensions are only as powerful as the permissions and scripts defined in their manifest file which acts as the blueprint. It's strange that marketplaces don't make manifest files more accessible prior to installation… so for now, we suffer.
While you can look at the manifest file on disk after installation, I’d recommend using a tool like Secure Annex that provides easy viewing and understanding of them.
You should be reading the manifest to understand the interdependencies of the extension like what information it has access to and what websites it can function on. Many extensions operate through their service worker (the brains), which can utilize permissions to access browser information, and content scripts, which are injected into webpages visited.
I’ll leave you to review what all of the possible permissions are capable of, but a handful are more impactful than others. Google published a white paper on the risks associated with each that you can use as a guideline. When many are present, toxic combinations are quickly formed.
It’s what’s inside that counts
After all that, you still might not know if an extension is good or bad. Malicious extensions may even functionally do most of what they claim to while tucking away some extra functionality within the extension package. These subtle behaviors can be difficult to detect as extensions run within the browser’s context and few tools have the ability to see within. Often the only visibility into extension behavior is a result of the chrome.exe process reaching out to any given websites… but that isn’t unusual at all!
Extensions are just files (mostly plaintext JavaScript) in folders on endpoints, which means you can utilize tools like YARA to scan for known suspicious patterns.
For extensions to access the most sensitive user information, like cookies, they must utilize well-known APIs that permissions provide access to. For instance, to take a screenshot of a tab, an extension would use the API chrome.tabs.captureVisibileTab() .
Here is a YARA signature that can detect the use of getting all cookies for a domain which can be a way to steal authentication sessions quickly.
rule Get_All_Cookies {
meta:
description = "Detect calls to the browser API to get all cookies"
author = "Secure Annex"
severity = "high"
strings:
$msg1 = /\.[a-zA-Z0-9_]*cookies\.getAll/ wide ascii
condition:
$msg1
}
Aren’t these just PUPs?
As Sydney points out, many extensions are harmless. Anything else has long only been thought of as simply potentially unwanted programs (PUPs). The reality is that bad extensions can be much more impactful, with many of their behaviors being incredibly hard to detect. A stolen authentication session can result in persistence through new account creation. Passwords inputs captured through content scripts will need to be continually rotated. Screenshots of financial documents could leak when all the CFO wanted to do was change the Salesforce font to Comic Sans.
If these hunting activities seem burdensome and difficult to roll out, try my tool, Secure Annex. It takes in all of this context to provide scoring of extensions combined with simple plaintext analysis of what an extension does. I also provide alerts when extensions change, as the extension you review today might not be the same one tomorrow!




Thanks for the article. It has me thinking about ways to investigate browser extensions.
This was a great read! Thanks for sharing John!