Hunting Beyond Indicators
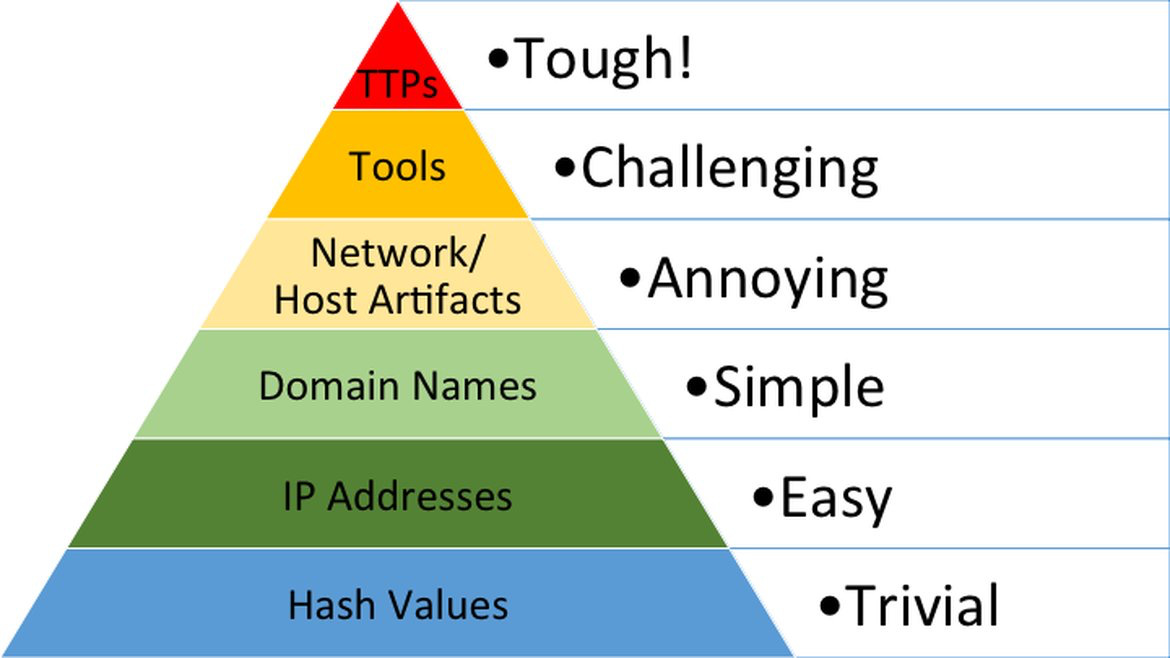
Indicators of Compromise (IOCs) are a powerful tool for security analysts and researchers to identify, track, and discover threat actor infrastructure and capabilities. However, threat hunting solely based on indicators leaves an organization one step behind adversaries - known (or related to known) malicious activity can be discovered, but unknown malicious activity will remain undetected. Furthermore, they are fragile - as popularized in David Bianco’s Pyramid of Pain, adversaries can easily change indicators with minimal hassle.
Indicator-based hunting is limited by its definition: if an indicator isn’t yet known to be bad, how could researchers identify its existence in a dataset? To close this gap, analysts must pivot to behaviors.
TTP-Based Hunting
By collecting data on adversary behaviors, such as those described in MITRE ATT&CK, we can potentially identify previously unknown activity that indicator-based hunting would likely miss.
There are some major advantages to focusing collection on TTPs:
Changing TTPs for an adversary is significantly harder to do, creating longer collection opportunities.
It is a significantly wider scope of investigation, enabling identification and tracking of multiple unrelated activity threads.
It can identify activity completely unknown to the community and organization.
There are disadvantages too. For one, the data you have access to significantly limits the behaviors you can hunt for. As such, organizations without the resourcing or collection capabilities may find TTP-based hunting less effective. Casting a wider net generates more false positives that analysts must triage, demanding extra resources. It also makes the process considerably more time-consuming, as hunts produce a much larger volume of results.
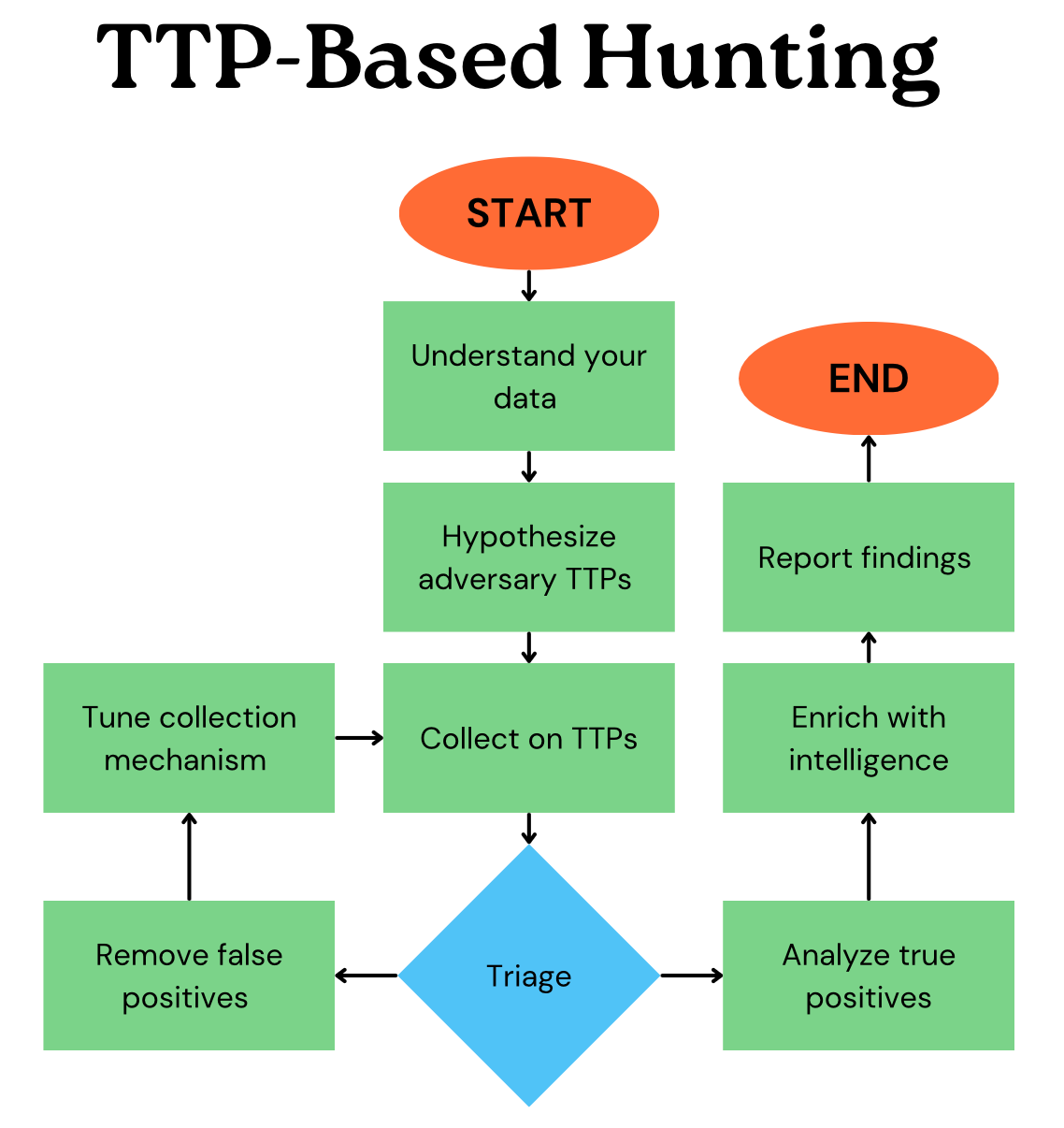
To get started, analysts must first understand the type of data they have access to, hypothesize adversary behaviors which could appear in their datasets, and engineer collection and triage mechanisms to efficiently collect, sort, and identify the most likely malicious candidates.
For example, an analyst with access to email data may hypothesize their organization has been targeted with phishing attacks and implement network monitoring rules to identify emails containing obfuscated JavaScript. In this case, the analyst has chosen to hunt based on MITRE ATT&CK T1027: Obfuscated Files or Information. Once collection of potentially malicious emails is completed, they may develop automated tools to remove common false positives occurrences in the dataset. Understanding of what caused false positives can inform analysts on how to improve and refine their collection mechanism. Dataset access, and therefore collection strategies, is highly dependent on the organization’s resourcing. For most threat hunting teams, data consists of a mix of 1st party data and external sources from threat intelligence providers, trust groups, partnerships, and more.
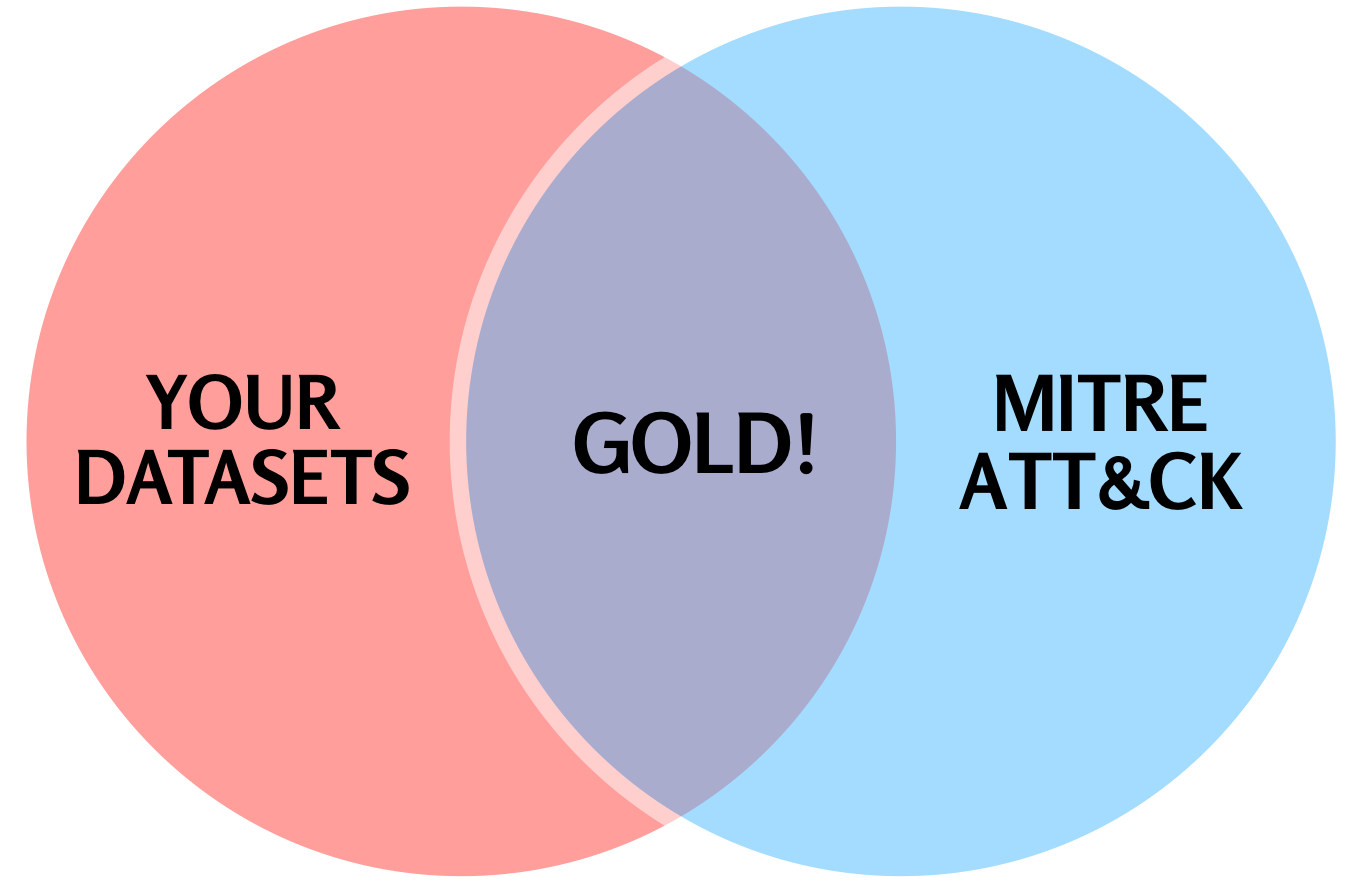
Collect on TTPs; Enrich with IOCs
While it may be tempting to keep the collection mechanism fairly strict, casting a wider net ensures maximum chances of capturing malicious artifacts and can often yield strong results, if the analyst is willing to triage and sort through more false positives. In that case, it is recommended to manually triage enough samples to learn how to properly automate the process.
Cast your net wide, then develop automated triage mechanisms.
Analysts are encouraged to use tools which synthesize different datasets like SIEMs or intelligence analysis tools like Vertex’s Synapse. By integrating disparate datasets, analysts can increase the context of the activity that they’re investigating and provide additional insights into whether an event is benign or malicious. Any connection discovered between the collected data and known-bad IOCs are incredibly suspicious and the newly collected artifact should be immediately investigated.
IOCs still provide great value to analysts, but are inherently focused on identifying known bad activity. TTP-based threat hunting can help by widening the aperture to catch activity that hasn’t yet been identified. The cost of triaging is the price of admission, but automation can help reduce the workload to manageable or even measly amounts.
“Give a CTI analyst an indicator, they’ll be fed for a day. Teach a CTI analyst to hunt for TTPs, and they’ll be fed for a lifetime”
We’ll put the TTP-based hunting methodology to the test, demonstrating how it can uncover unique finds with a hacktivist-related capability used to gain unauthorized access to Human-Machine Interfaces. Stay tuned for part 2 of this blog series!