See Evil, Thrunt Evil – Modelling Behaviors is a Critical Thrunting Prerequisite
In the previous THOR Collective Dispatch posts, Sydney and Lauren explored the importance of planning your way into a thrunt – especially data collection. We’ll connect back to their insights at the end of this post, but I 100% cosign the step 0 prioritization on planning.
Even as plans fail evolve, the time invested in preparation still pays dividends – especially compared to an unstructured “operational improvisation™” approach (😱). In this post we’ll explore a different angle to planning, focusing instead on the target of the thrunt.
So what do we actually thrunt? I have certainly encountered scenarios where it made a lot of sense to focus on a specific threat – whether it be a named actor or family of malware. But generally, thrunts should focus on behaviors.
Even if you are scoping a thrunt to chase a lead on a specific actor, it is still advantageous to decompose your focus into more tangible behaviors (if only this was easy as SELECT * FROM logs WHERE event LIKE `APT29`).
But what really is a behavior?
How to Model a Behavior (yeah this is going to be more than one technique…)
One of the most important concepts towards truly seeing and understanding behaviors is embracing the reality that what we think of as real-world “techniques” are really compounds of multiple actions. Jared Atkinson has an excellent series of blogs that unpacks a similar concept towards an objective answer to “what is a procedure?” (or a unique instance / implementation of a technique).
The high-level takeaway is that adversary behaviors are not executed in isolation. When we see or think about “techniques,” we really need to be decomposing and considering all the distinct mechanics that go into the malicious activity.
This modeling is critical towards scoping and preparing for a successful thrunt. Modelling is definitely as much an art as it is a science, so never stress doing it “right” vice the way that works best for you.
Let’s take a look at a few examples of the behavior models that can drive our thrunting.
Example 1 – Remote Exploitation (the edge ™)
If we set out to uncover evidence of exploitation of Internet-facing assets (e.g., edge devices, web servers, oh my…), we can absolutely focus on the specific vulnerability in the form of unique strings or other artifacts. But we can also more broadly model this behavior without even thinking about a specific CVE (or even 0-days).
Katie Nickels delivered an excellent talk at ShmooCon 2024 that explored the challenges of over-prioritizing defending the exploitation itself, vice the entirety of the adversary’s chain of activity.
Embracing this concept highlights a better approach to thrunting exploitation. While the vulnerability specific artifacts can be helpful, can we instead cast a broader net for the pattern of all exploitation activity?
As we can see in this simple model, this behavior is not just a single technique. Behaviors are instead an interconnected series of techniques that are often multiple primitive actions coupled together in unique ways.
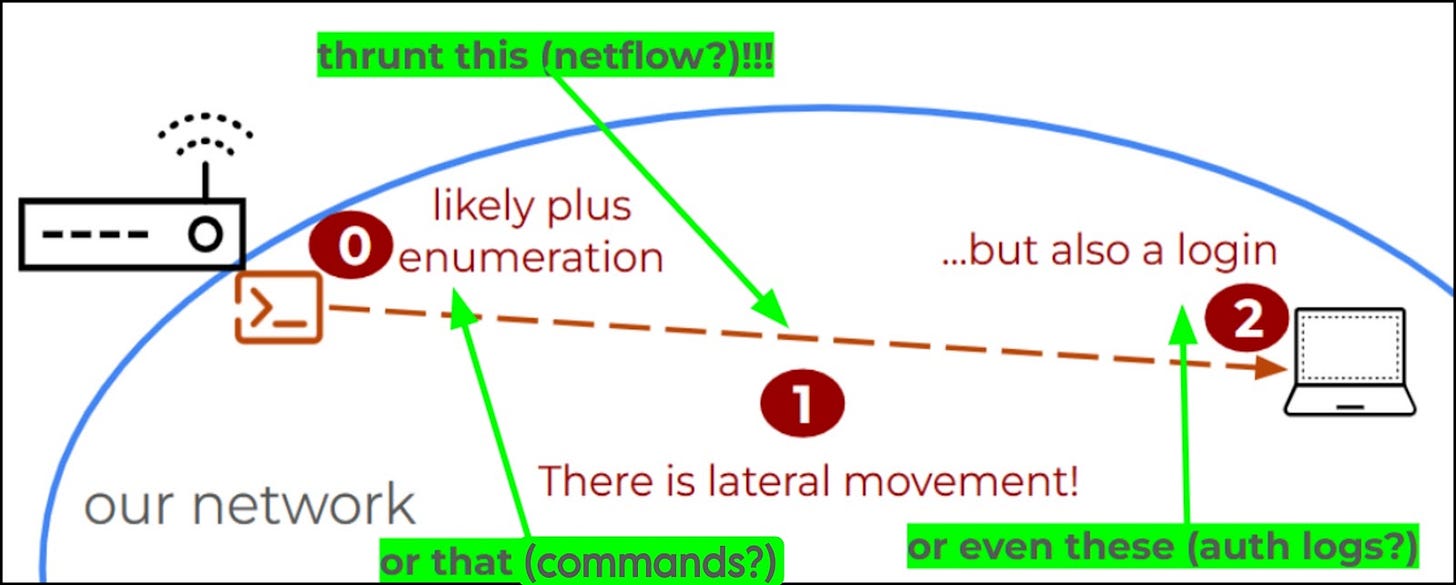
Example 2 – Lateral Movement ( 🛋️ PIVOT🛋️)
As another example, we can abstract this behavior modeling beyond techniques to almost consider an entire tactic.
Bringing These Models Back to the Thrunt (& connecting to data sources)
How does this modelling connect back to planning for a thrunt? Once we can actually see and understand the behaviors we are seeking, connecting these models to data sources highlights where/when/how these malicious behaviors will appear in potentially available telemetry.
So before you start caffeinating and hammering on the keyboard looking for APT-level tradecraft (🫡), take some time to sketch out what that badness really looks like.
*& don’t forget to thank your SOC analysts every chance you get ❤️