Aligning Risk Management and Threat-Informed Defense Practices (Part 2)
We’re back with part two of a series analyzing how to align common GRC tasks/teams with SecOps and threat-informed defense practices. In Part 1, which can be viewed here, we covered the what behind this concept. Quick overviews of the objectives for common GRC and threat-informed defense tasks were presented, along with information on MITRE ATT&CK. In this blog we will dive into why siloed GRC/SecOps teams can harm organizational effectiveness, and when it makes sense for an organization to align these functions.
Issues When Teams Are Siloed
GRC can get a bad rap in security circles, at times it can be deserved. Unfortunately most GRC processes have not stayed up to date with current workflows. And many of us have heard the phrase “compliance ≠ security.” Look, no one wants to upload another screenshot of a setting or write paperwork in hopes one person will eventually look at it and give the thumbs up. But guess what, compliance teams hate it when the SecOps or CTI output looks like a bunch of random noise that can’t be used to verify anything. These teams speak different languages and have different goals. But, all hope is not lost. By aligning GRC and SecOps, creating common languages and goals, you’re teams can go from this
To singing “you’ve got a friend in me.” In this manner these teams can work together to help the organization remain compliant, secure, and efficient.
It’s true that compliance probably won’t provide sufficient security if the business stops at meeting minimum requirements to check a box, pass an audit, or align with a standard. But, if compliance serves as a starting point toward a more mature security program, it can contribute to improving security.
And while it’s easy to point the finger at compliance, SecOps doesn’t get off the hook here. If lessons learned from incidents don’t feed back into governance, the same mistakes repeat because controls never change. Without a good understanding of all expected controls, it’s difficult to best judge where mitigations exist, or what constitutes a concerning alert that has bypassed those controls. If GRC and SecOps don’t share data, analysts are likely to miss the “so what?” of an incident.
Why Align?
We can all agree that cyber risks and threats continue to evolve and grow year over year, attempting to disrupt how we do things. With greater innovation and interconnectedness, has come greater opportunities for digital security to positively or negatively impact businesses. The key to staying ahead has come down to acting on intelligence. Which side can proactively anticipate the other, and make (or prevent) the next move?
During battle, the side with the most knowledge and strongest ability to act according to that knowledge often has the best odds of coming out on top. No soldier wants to be on the less informed side when lives are on the line. The same is true in the cyber realm. It has become increasingly clear that strategic, tactical, and operational intelligence is the greatest asset a defender can hold. Knowledge of self, knowledge of the enemy, and knowledge of how to use that information to gain an advantage (once again, is it even a cyber blog if Sun Tzu doesn’t appear?). For years, the approach to cyber has been reactive. Attempting to block or alert on IOCs (Indicators of Compromise) such as known-bad websites, files, or hashes. As the number of ransomware attacks and breaches continues to rise, it can be understood that this approach is lacking. IOCs can change on the dime, making it impossible to catch every IP or hash change (Pyramid of Pain joke, we want to inflict pain on the adversary, not on ourselves). The strategy of implementing defensive controls to keep out all cyber threats is also unrealistic and impractical. There are too many threats to defend against, too many alerts to analyze, and the costs associated with remaining uninformed keep growing. A reactive cybersecurity strategy will continue to cost organizations.
Now that we understand some of the frameworks at hand (ATT&CK and RMF), why should an organization combine the two? What is the benefit of a risk managed and threat-informed defense?
The goal behind this strategy is to switch, (or as I like to think of it, level up) from the wishful (and very exhausting) compliance-driven strategy of doing the bare minimum to meet cybersecurity compliance requirements, and hoping to defend against every cyber threat that exists. The desired end state will be a proactive defense that uses the knowledge of dangerous threats which are specific and most relevant to the organization/industry to tailor and then test defensive controls against those adversary behaviors. Breaking down the GRC/TID silos can sync defensive teams, enabling larger strategic initiatives to be developed.
The issues with relying solely on risk management for security is that a compliance framework is incapable of changing at the speed that threats do. NIST 800-53 rev 4 was released in 2013. As of 2023, it was still the requirement for most RMF specific assessments. Finally now in 2025 most have migrated to rev 5, released ONLY 5 years ago (remember the days before AI, yeah way back then). The main problem with a compliance approach is that a compliant system is not by default also a secure system. Most systems that undergo a compliance validation process are never properly tested against the threats to that system. Screenshots don’t compare so well to command execution or lateral movement. Another issue in only using compliance metrics to measure security is that compliance frameworks are meant to provide a broad scale of security for a wide range of users, it is not specific to an organization’s needs. It is ultimately up to each organization to take action to become secure by knowing their threats and risks, and testing/validating that defenses protect against the threats that could bring them the most harm.
Control frameworks adequately addresses the reduction of risk through implementation of security controls, however, they do not take into consideration specific threats or threat actor behaviors/TTPs. Meanwhile, CTI and MITRE ATT&CK is great for identifying threat behavior, but organizations will still need to act on that knowledge by implementing cyber defenses and controls.
A more effective cybersecurity posture can be achieved by combining the compliance framework with the knowledge found in ATT&CK and CTI to create a holistic, risk-managed and threat-informed cyber defense strategy. The control framework creates a deep knowledge of self, while ATT&CK/CTI grants knowledge of the adversary. Combined, they allow an organization to know the enemy, know security defenses, and act according to that knowledge to defend against the adversary, even before the adversary strikes.
When aligning GRC with threat-informed defense practices, an organization can create a proactive, holistic cyber defense strategy that:
Knows the relevant risks and threats facing the organization (threat profile)
Identifies what has been done to reduce risk and mitigate known threat actor behavior
Verifies proper control implementation and coverage
Achieve compliance with validated defenses against known threats
Can detect and protect against real-life attacks
Locates issues and reduces potential impact prior to an attack
Uses intelligence to connect threats, risks, controls, and business objectives
WHEN
So, we have identified that it is a good idea to combine governance, compliance, and risk management with threat knowledge, but how is it done well? When and where should an organization begin when combining these two frameworks into a defensive strategy?
The first step should be to receive upper management support. An effective roll-out of this process will require culture and procedural changes, and it needs to be supported from the top.
Next, an organization needs to be honest with their current maturity level. If you are still working to implement MFA, it’s probably not the time to be standing up a CTI function. Basics first, then focus on relevant threats and risks.
Anton Chuvakin wrote a fantastic piece on the challenges of operationalizing threat-informed defense. He listed out a few common problems within organizations who do not align strategies across teams. While the full blog can be found here: https://medium.com/mitre-engenuity/threat-informed-defense-is-hard-so-we-are-still-not-doing-it-31ae7b68955f, a quick rundown is provided below.
“To start, one can say that foundational levels of security are not and perhaps even should not be threat-centric. After all, much of basic security is just good engineering, no? Threat-informed defense should be built upon foundational cyber-hygiene.
Ironically, the “cyber-havenots” are less likely to practice threat-informed security while they are the ones who can benefit the most from focusing their scarce resources on threats that matter! Basics matter, but basics prioritized by real threats are better!
Poor quality of threat intel makes organizations unwilling and unable to make decisions off their collected threat data. Threat intelligence is often incomplete, inaccurate, or outdated, and this makes it difficult for organizations to make informed security decisions.
Outside of security, immature IT capabilities ruin threat-informed defense. If your IT asset management, change management, etc. are inflexible, silo’d, hostile to security, your defenses can probably only be static and unchanging.
Sometimes, the bridge from threat intelligence to security controls isn’t conceptualized, built or practiced. The organizations have threat intel in one bucket, and their security controls in another.
Organizations also lack the types of personnel that can turn threat knowledge into improved defenses or drive threat-informed changes to defense approaches they practice.
Compliance culture is focused on building static, auditor-proof defenses. A shift in security culture is often required to adopt a threat-informed approach and this is hard for many organizations, large or small.
Narrow use case around threats: organizations only practice threat-informed detection, but not the rest of security”
So, we can see it takes personnel, culture, existing foundational levels of security and IT hygiene, and quality threat intelligence prior to finding value in deploying threat-informed or threat-centric defenses.
Here is my list of “must have’s” an organization absolutely will need before really jumping into the threat-informed defense + GRC game.
Required or identified compliance framework that will act as the baseline
Some security / IT maturity (asset inventory, basic defensive engineering controls)
Logs, some type of SIEM / query capability
Detection (defend) capability, usually in the form of EDR/SIEM
Testing (attack) capability, this can be manual or via automated BAS tools
Identified attack chain(s) or atomic TTPs (relevant CTI)
At this point, an organization will also need to identify a team or individual to manage threat-informed defense across the organization. This team needs to be given authority to make changes where necessary and shift the processes and tools that need to go or be modified. Ideally this would be a couple members from multiple teams (GRC, Detection Engineering/SecOps, CTI, Red Team).
Quick example, when looking at the Risk Management Framework, incorporating threat information would begin in step 2 (Select Controls) and continue throughout the life cycle of the system. When selecting controls, the organization should aim for that control to address both compliance requirements and prevent or detect adversary behavior. However, as adversaries change, so should defenses and controls. Maintaining up-to-date knowledge is integral to a threat-informed cyber defense.
Provided below are some questions to ask when getting started with threat-informed defense. These are by no means extensive, only serving as guidelines for identifying which techniques to focus on. It is highly encouraged to tailor questions to your specific organization and mission needs.
What threat actors commonly target my industry?
What techniques are used by these groups?
What controls do we currently have in place?
What controls are we confident in, and which ones are we less certain of their effectiveness?
What are our crown jewels (business-critical functions, information, and systems) that we must protect?
Who are the stakeholders that require CTI and GRC outputs?
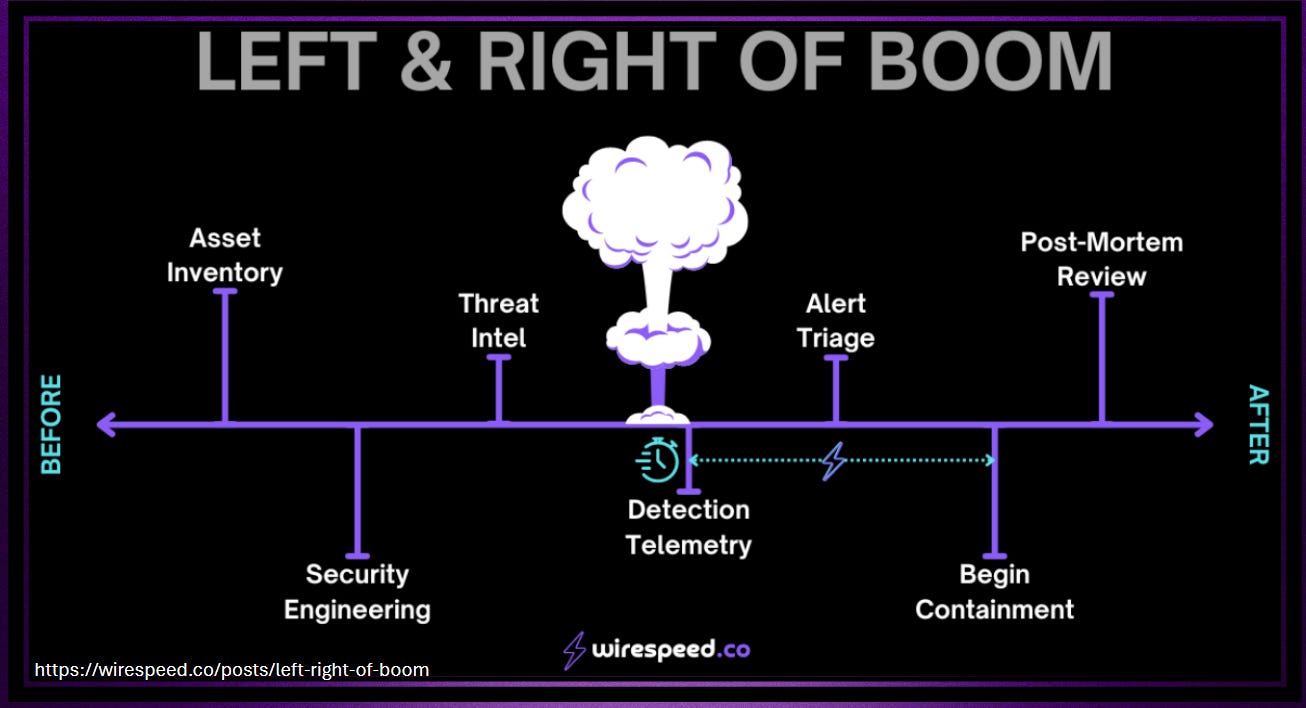
I really enjoy the following graphic from Wirespeed (who was just recently purchased by Coalition, congrats to them) which depicts actions of security teams before and after the detection of an attack has occurred.
This graphic really helps to visualize the timeline of what occurs prior to detection, and then afterwards all the way through containment and post incident review.
In the next post we’ll discuss the how to and offer some ways an organization might approach integrating GRC with threat-informed defense. I’ll also share some free tools that can help with some of the processes, and finally take a look into so what could this really mean for an organization?