The PEAK Threat Hunting Template You'll Wish You Had Sooner
Because screenshots of queries aren’t documentation.
If you’ve ever completed a great hunt and completely forgotten what you did two weeks later, this template is for you.
Maybe you pieced together queries across five tabs, made mental notes during a caffeine-fueled hyperfocus, and promised to write it up later. We’ve all been there.
But good hunts deserve better.
They deserve structure. They deserve documentation. They deserve to be repeatable, reviewable, and shareable.
That’s why we built a threat hunting template grounded in the PEAK Threat Hunting Framework. So your hunts don’t get lost in Slack threads, screenshots, or brain fog.
This template builds on ideas from our earlier posts, AI is My Bestie and Agentic Threat Hunting, Part 2, taking the next step toward structured, AI-ready documentation for threat hunters.
This template walks through the full threat hunting lifecycle using PEAK (Prepare, Execute, Act with Knowledge). It’s structured for real-world use: collaborative hunts, repeatable documentation, and clear readouts for SOC, IR, Threat Intel, and Detection Engineering.
Want a copy?
Click here or scroll down to grab the full template below.
What’s Inside
Threat Hunting Report – PEAK Framework
Hunt ID: H/B/M-XXXX
(H for Hypothesis-driven, B for Baseline, M for Model-Assisted)
Hunt Title:
A concise, descriptive name for this hunt.
PREPARE: Define the Hunt
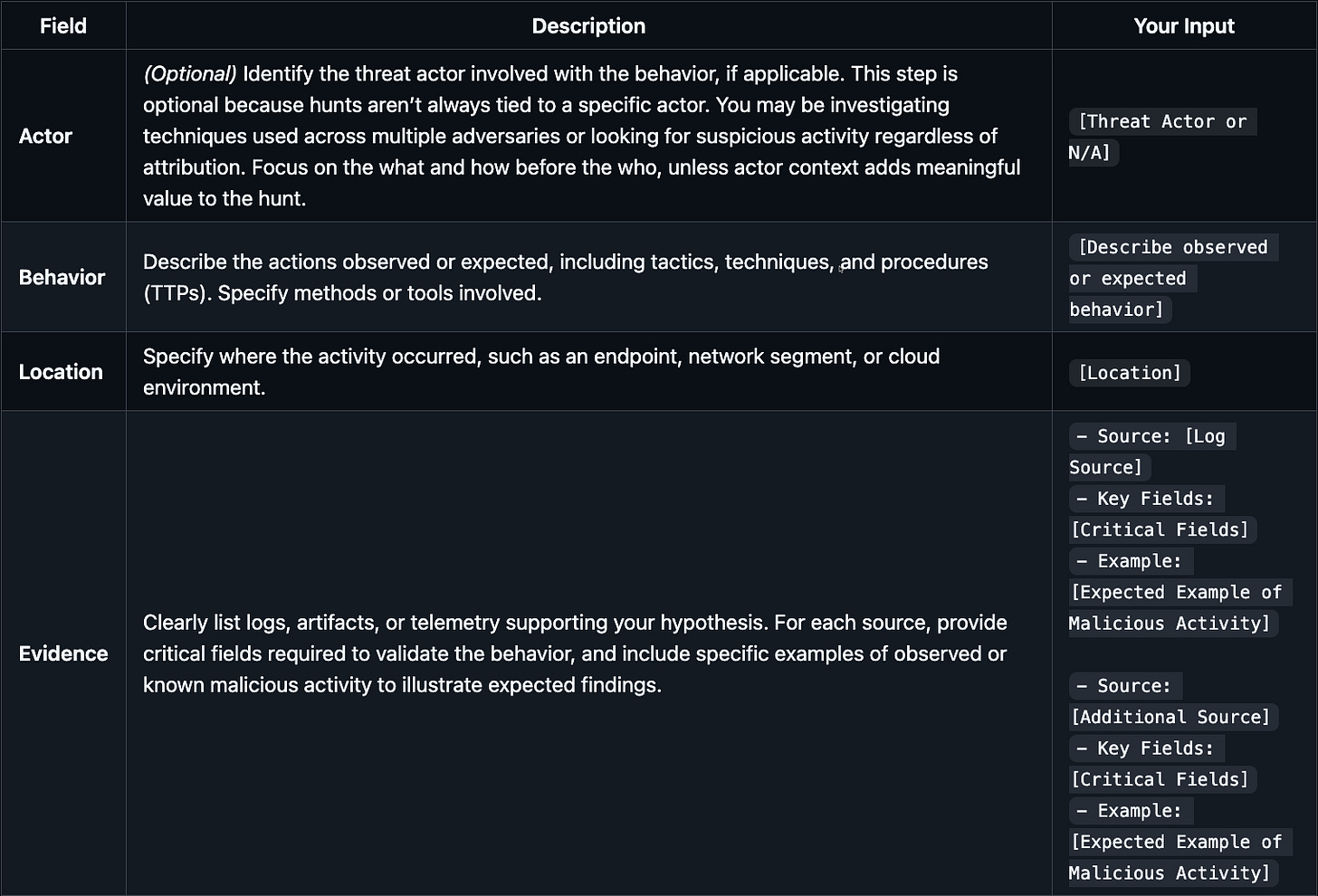
Scoping with the ABLE Methodology
Clearly define your hunt scope using the ABLE framework. Replace all placeholders ([ ]) with relevant details for your scenario.
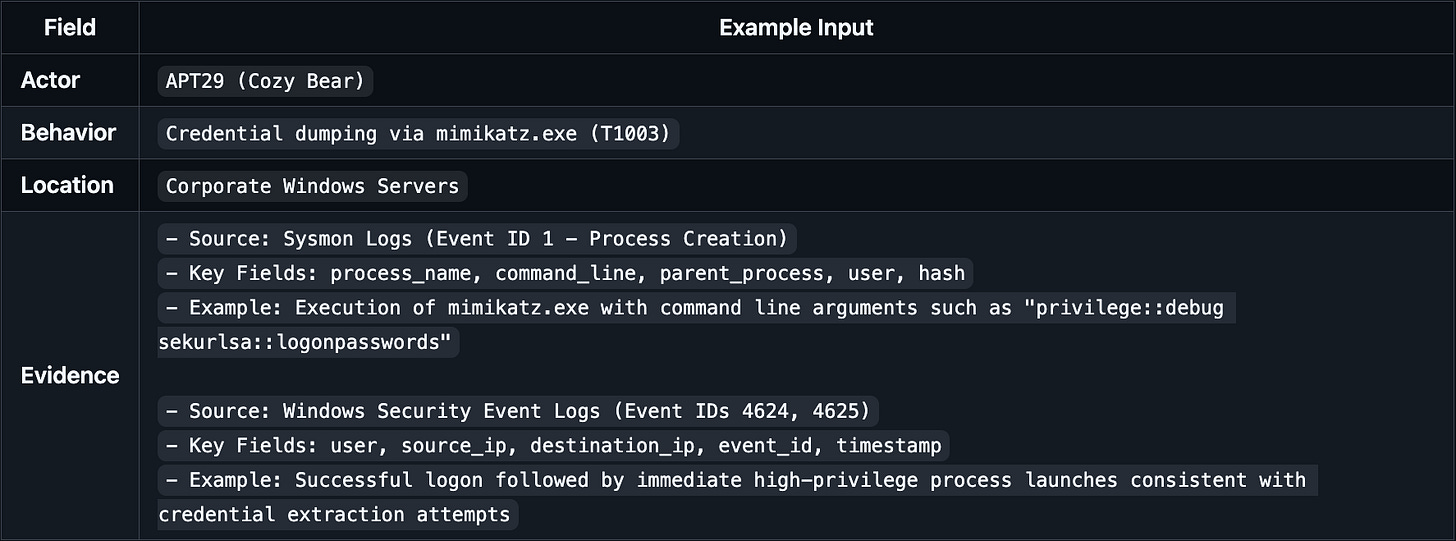
Example ABLE Inputs
Related Tickets
(detection coverage, previous incidents, etc.)
Threat Intel & Research
MITRE ATT&CK Tactics, Techniques, & Procedures (TTPs):
TAxxxx - Tactic Name
Txxxx-Technique Name
Related Reports, Blogs, or Threat Intel Sources:
[Link][Reference]
Historical Prevalence & Relevance:
(Has this been observed before in your environment? Are there any detections/mitigations for this activity already in place?)
EXECUTE: Run the Hunt
Hunting Queries
(Document queries for Splunk, Sigma, KQL, or another query language to execute the hunt. Capture any adjustments made during analysis and iterate on findings.)
Initial Query
index=thrunt sourcetype=linux:audit "sudo" OR "pkexec"
| stats count by user, command, parent_processNotes:
Did this query return expected results?
Were there false positives or gaps?
How did you refine the query based on findings?
Refined Query (if applicable)
index=thrunt sourcetype=linux:audit "sudo" OR "pkexec"
| stats count by user, command, parent_process, _time
| sort - _timeRationale for Refinement:
Added
_timefor better event sequencing.Applied
sortto identify patterns in privilege escalation attempts.
Visualization or Analytics
(Describe any dashboards, anomaly detection methods, or visualizations used. Capture observations and note whether visualizations revealed additional insights. Add screenshots!)
Examples:
Time-series charts to detect activity spikes
Heatmaps of unusual application installs
Detection Logic
(How would this be turned into a detection rule? Thresholds, tuning considerations, etc.)
Initial Detection Criteria:
What conditions would trigger an alert?
Are there threshold values that indicate malicious activity?
Refinements After Review:
Did certain legitimate activities cause false positives?
How can you tune the rule to focus on real threats?
Capturing Your Analysis & Iteration
Summarize insights gained from each query modification and visualization.
Reiterate key findings:
Did this query lead to any findings, false positives, or security incidents?
If this hunt were repeated, what changes should be made?
Does this hunt generate ideas for additional hunts?
Document the next steps for refining queries for detections and other outputs.
ACT: Findings & Response
Hunt Review Template
Hypothesis / Topic
(Restate the hypothesis and topic of the investigation.)
Executive Summary
Key Points:
3-5 sentences summarizing the investigation.
Indicate whether the hypothesis was proved or disproved.
Summarize the main findings (e.g., "We found..., we did not find..., we did not find... but we did find...").
Findings
(Summarize key results, including any unusual activity.)
KNOWLEDGE: Lessons Learned & Documentation
Adjustments to Future Hunts
What worked well?
What could be improved?
Should this hunt be automated as a detection?
Are there any follow-up hunts that should be conducted?
What feedback should be shared with other teams (SOC, IR, Threat Intel, Detection Engineering, etc.)?
Sharing Knowledge & Documentation
(Ensure insights from this hunt are shared with the broader security team to improve future hunts and detections.)
Knowledge Base (KB) Articles
Write an internal KB article that captures:
The hunt's objective, scope, and key findings
Any detection logic or rule improvements
Lessons learned that are relevant for future hunts or incident response
Document newly uncovered insights or patterns that could benefit SOC, IR, or Detection Engineering teams, especially anything that could inform future detections, playbooks, or tuning decisions.
Threat Hunt Readouts
Schedule a readout with SOC, IR, and Threat Intel teams.
Present key findings and suggested improvements to detections.
Reports & External Sharing
Publish findings in an internal hunt report.
Share relevant insights with stakeholders, vendors, or industry communities if applicable.
References
[Insert link to related documentation, reports, or sources]
[Insert link to any external references or articles]
AI Ready Hunts
One of the most powerful parts of this template is that it is not just for humans. It is AI friendly. In Agentic Threat Hunting, Part 2, I argued the first step toward agentic hunting is not plugging AI directly into Splunk, it is giving it memory. When your PEAK hunts live in structured markdown in a GitHub repo with an AGENTS.md, they become something AI can actually learn from. AI can summarize hunts, suggest query variants, map to ATT&CK, or even generate new hypotheses. That makes this template versatile. It is useful for your team today and it is fuel for your AI bestie tomorrow.
Want a Copy?
Whether you’re documenting a YOLO hunt postmortem or building a hunting playbook from scratch, this template is here to help you do it on purpose. And because it’s structured, you can throw it into AI and get support on summarizing, remixing, or scaling your hunts. That’s what makes it versatile: useful now, and ready for the next wave of agentic hunting.
You can grab the template as a Google Doc here or from our GitHub to adapt it for your team.
Try it on your next hunt.
Share how you adapted it.
Tag us or drop a comment below!
Stay curious and happy thrunting! 🐏







Splendid! Will be using this.